There seems to be a number of sites using non standard port numbers for some reason or other. For example: http://www.sismologia.cl:8000/ Why does anyone think this is a good idea? Don’t developers and designers realise that, for very valid security reasons, many companies restrict outbound traffic to common ports such as TCP/80 and TCP/443? Why make it hard for your customers?
It’s just not good enough!
Saturday 10 March 2012
WSUS and Multiple Reboots
I had to update a Windows 2003 server that hadn’t been updated in a fair while. The server gets its updates from WSUS. Each time I clicked on the Windows Update icon in the task bar Windows went off and downloaded and installed updates from the WSUS server (including Service Pack 2). After the updates had been installed I was invariably asked to reboot the server. After each reboot there would be more updates to install.
So far I have had to reboot the server five times. That means that its gone off to WSUS and downloaded five sets of updates (actually six, it also downloaded and installed the latest RDP client but that didn’t require a reboot).
Why do I need all these reboots? Why do I have to update it multiple times? Why can’t it download and install all the required updates together – like Linux does? If this server had been running Red Hat or Debian or Ubuntu I would have only needed to update once – and rebooted once. Instead it’s taking me hours.
It’s just not good enough!
So far I have had to reboot the server five times. That means that its gone off to WSUS and downloaded five sets of updates (actually six, it also downloaded and installed the latest RDP client but that didn’t require a reboot).
Why do I need all these reboots? Why do I have to update it multiple times? Why can’t it download and install all the required updates together – like Linux does? If this server had been running Red Hat or Debian or Ubuntu I would have only needed to update once – and rebooted once. Instead it’s taking me hours.
It’s just not good enough!
BSOD when updating ATI drivers on Windows 7 64 bit
I have an ATI Radeon HD 2400 Pro video card. Back in October I attempted to install the latest ATI drivers in the hope that it would resolve a problem I was having (I was previously using the drivers that came with Windows 7). I downloaded the lasted driver at the time (9.9) from the ATI website and then ran the install. Imagine my surprise when I got the following (sorry about the image quality, I used the camera on my phone):
It turns out that I wasn’t the only one getting these blue screens of death. I think it’s totally unacceptable that a major hardware vendor can release drivers or software that cause a BSOD of death during install. Don’t they test these things?
Since then ATI have released newer drivers. I have successfully managed to install version 9.11 – although it didn’t fix the problem. However. that doesn’t change the fact that ATI released drivers that not only wouldn’t install, but crashed Windows.
It’s just not good enough!
 |
| BSOD when installing ATI Drivers |
It turns out that I wasn’t the only one getting these blue screens of death. I think it’s totally unacceptable that a major hardware vendor can release drivers or software that cause a BSOD of death during install. Don’t they test these things?
Since then ATI have released newer drivers. I have successfully managed to install version 9.11 – although it didn’t fix the problem. However. that doesn’t change the fact that ATI released drivers that not only wouldn’t install, but crashed Windows.
It’s just not good enough!
Black screen (no signal) after RDPing to PC running Windows 7 64 bit
I have a PC running the 64 bit edition of Windows 7. The PC has an ATI Radeon HD 2400 Pro with two 19″ HP LCD screens attached. I have a problem where the left screen reports no signal in the following scenario:
I have a colleague with an almost identical PC . The only difference is that he has an Intel graphics card. He doesn’t get this problem.
I have tried the latest ATI drivers but it made no difference. I have also tried an update from Microsoft which didn’t fix the problem either.
It’s just not good enough!
Update: A workaround is available at http://www.tipsandscripts.net/archives/68
- The screens are put to sleep by Windows
- I connect to the computer using Remote Desktop
I have a colleague with an almost identical PC . The only difference is that he has an Intel graphics card. He doesn’t get this problem.
I have tried the latest ATI drivers but it made no difference. I have also tried an update from Microsoft which didn’t fix the problem either.
It’s just not good enough!
Update: A workaround is available at http://www.tipsandscripts.net/archives/68
BlueCoat/Packeteer PolicyCenter, PacketShapers and attrib iqosClassID errors
BlueCoat PacketShapers can be configured individually, or from a central management server called PolicyCenter. If you have more than a few PacketShapers it can be easier to use PolicyCenter.
PacketShapers have a hierarchical configuration – the class tree. Each class has a 31 bit unique ID – the iqosClassID attribute. If you’re using PolicyCenter you can create hierarchical configurations that your PacketShapers can inherit. So, you might have somethink like:
MPLS-Sites/SanFran/sfps01
where sfps01 is a PacketShaper, and MPLS-Sites and SanFran are configurations. A setting in MPLS-Sites will be inherited by SanFran and then by sfps01. A setting in SanFran will be inherited by sfps01. Of course, a child configuration can override a parent configuration.
When you create a class in MPLS-Sites it automatically gets given a Class ID. The problem is that PolicyCenter does nothing to make sure that the Class ID created is unique. So, you may create a new class in MPLS-Sites and end up with an error like
Configuration error in /MPLS-Sites/SanFran/ZAJNBA/204-10000111, object /Outbound/NewYork, attrib iqosClassID = “1208514799″, 1208514799 is already in use by class “/Outbound/VoIP”.
It’s just not good enough!
PacketShapers have a hierarchical configuration – the class tree. Each class has a 31 bit unique ID – the iqosClassID attribute. If you’re using PolicyCenter you can create hierarchical configurations that your PacketShapers can inherit. So, you might have somethink like:
MPLS-Sites/SanFran/sfps01
where sfps01 is a PacketShaper, and MPLS-Sites and SanFran are configurations. A setting in MPLS-Sites will be inherited by SanFran and then by sfps01. A setting in SanFran will be inherited by sfps01. Of course, a child configuration can override a parent configuration.
When you create a class in MPLS-Sites it automatically gets given a Class ID. The problem is that PolicyCenter does nothing to make sure that the Class ID created is unique. So, you may create a new class in MPLS-Sites and end up with an error like
Configuration error in /MPLS-Sites/SanFran/ZAJNBA/204-10000111, object /Outbound/NewYork, attrib iqosClassID = “1208514799″, 1208514799 is already in use by class “/Outbound/VoIP”.
It’s just not good enough!
Cisco Unified Communications Manager and LDAP Integration
Cisco Unified Communications Manager v6 (formerly called Call Manager and then Unified Call Manager) can synchronise its user list with Active Directory (it’s actually a one way synchronisation), and can authenticate users against Active Directory. It does this using LDAP. That’s no surprise and pretty standard. Unfortunately, it doesn’t allow you to specify any search filters. You specify the base DN (or multiple base DNs) and that’s it. It seems that if an account in AD has a first name and last name CUCM adds it to its directory. The account doesn’t need to have a telephone number, it can even be disabled. Note that you can only synchronise accounts – CUCM ignores Contacts.
Didn’t anyone at Cisco think that their clients might possibly want to filter their imports? Did it not occur to them that the structure in AD might not reflect the way clients want to import users into CUCM?
It’s just not good enough!
Didn’t anyone at Cisco think that their clients might possibly want to filter their imports? Did it not occur to them that the structure in AD might not reflect the way clients want to import users into CUCM?
It’s just not good enough!
Sorting Columns – Microsoft SQL Server 2000 Enterprise Manager
Opened up SQL 2000 Enterprise Manager the other day to look at a performance problem (which turned out to be someone purging WSUS of old updates). Anyway, I went to look at Process Info (under Management –> Current Activity) to see what was happening. Process Info displays details on various SQL process IDs (e.g. Open Transactions, CPU, Physical IO, Memory Usage). It also lets you sort by various columns – which can be quite useful. I say “can be”, because, unfortunately, Enterprise Manager seems to do an ASCII or alphanumeric sort, rather than a numeric sort:
What bright spark went to all that trouble to provide all this information in Process Info, and then didn’t do the last bit to allow us to sort it in an intelligent manner. I mean, it can’t be that hard.
It’s just not good enough!
 |
| Process Info sorted by CPU |
What bright spark went to all that trouble to provide all this information in Process Info, and then didn’t do the last bit to allow us to sort it in an intelligent manner. I mean, it can’t be that hard.
It’s just not good enough!
Trend Micro Office Scan causing the System process to use excessive CPU
I had a server run low on disk space on one of the data volumes (a bit over 1 GB free on a 2 TB volume). When this happened, CPU utilisation went up to 100%. Task Manager showed System was the offending process. This is not the first this has happenedto us (although it’s the first time I’ve looked at it).
So, I ran Process Explorer on the server and took a look at the threads for the System process. Here’s what I saw:
It turns out TmXPFlt.sys is part of Trend Micro Office Scan’s virus scan engine. I tried unloading Office Scan but it made no difference. In the end I had to restart the server.
We install anti-virus to protect our servers, not to take them down.
It’s just not good enough!
So, I ran Process Explorer on the server and took a look at the threads for the System process. Here’s what I saw:
It turns out TmXPFlt.sys is part of Trend Micro Office Scan’s virus scan engine. I tried unloading Office Scan but it made no difference. In the end I had to restart the server.
We install anti-virus to protect our servers, not to take them down.
It’s just not good enough!
Highway Robbery
We have some spare slots in an IBM EXP810 disk tray attached to our DS4000 series storage system and thought of filling them with 1TB SATA disks. MCG Technology have 1TB Seagate drives (ST31000340AS) for $179 including tax (or 16c per GB). Note that these drives come with a 5 year warranty. So I figured a drive from IBM would probably be around the $500 mark. That would allow for an enterprise spec’ drive, the enclosure and IBM’s usual exorbitant markup.
Boy was I wrong.
Our Australian dollar ex-tax purchase price for a 1000 GB/7.2K SATA EV-DDM drive is $2100.00 each. I couldn’t believe it. That works out to $2.10 per GB – and they’re not proper sized gigabytes either.
By contrast a 750GB SATA drive from IBM comes to $850.00 or $1.13 per GB.
Now I know that the world is in a financial crisis. But that doesn’t excuse IBM ripping its customers off. It appears that the robber barons of Wall Street have moved to 1 New Orchard Road.
It’s just not good enough!
[Edited to add]
Seagate have an enterprise SATA 2 1TB disk – the Barracuda ES.2 ST31000340NS. The cheapest price on staticICE is $299
Boy was I wrong.
Our Australian dollar ex-tax purchase price for a 1000 GB/7.2K SATA EV-DDM drive is $2100.00 each. I couldn’t believe it. That works out to $2.10 per GB – and they’re not proper sized gigabytes either.
By contrast a 750GB SATA drive from IBM comes to $850.00 or $1.13 per GB.
Now I know that the world is in a financial crisis. But that doesn’t excuse IBM ripping its customers off. It appears that the robber barons of Wall Street have moved to 1 New Orchard Road.
It’s just not good enough!
[Edited to add]
Seagate have an enterprise SATA 2 1TB disk – the Barracuda ES.2 ST31000340NS. The cheapest price on staticICE is $299
ldapsearch and Line Width
OpenLDAP is open source LDAP software. It’s used on a lot of Unix and Linux distributions. ldapsearch is a utility that comes with OpenLDAP. It allows you to search an LDAP directory from the command line. This is potentially very useful when you need to access an LDAP directory from a shell script. You can even use it to access Active Directory, as Phil Lembo shows here.
Unfortunately, when ldapsearch returns its results it wraps the output after 76 characters – and it doesn’t appear to give an option to turn line wrapping off. Now what bright spark thought that this would be a good idea. That makes it a pain in the arse when you’re trying to grep the output of a directory search.
Someone does seem to have come up with a patch back in 1999, but it doesn’t appear to have made it into production.
It’s just not good enough!
Unfortunately, when ldapsearch returns its results it wraps the output after 76 characters – and it doesn’t appear to give an option to turn line wrapping off. Now what bright spark thought that this would be a good idea. That makes it a pain in the arse when you’re trying to grep the output of a directory search.
Someone does seem to have come up with a patch back in 1999, but it doesn’t appear to have made it into production.
It’s just not good enough!
Useless Error Messages
I went to shut my computer down last night and received the following error (it turns out that “No” was the option I wanted – “Yes” didn’t seem to do anything):
It’s just not good enough!
It’s just not good enough!
Why Isn’t There an Option to Confirm Drag and Drop in Windows?
Ah, criticising Microsoft is a bit like picking on the disabled kid.
Anyway, one of the issues we have with Windows is when a user accidentally moves a directory. How do you accidentally move a directory you ask. By moving your mouse across the screen. Sometimes, for one reason or another, as you drag the mouse the left button gets held down and suddenly you’ve moved a directory. If it’s a small directory the user may not even be aware that they’ve done it – and sometime later we get asked to restore the “missing” directory.
This has happened often enough that I’ve been asked to modify permissions on directories so that users can’t do it. The problem is I can’t – the permissions on the directories are fine. The users concerned are supposed to be able to do what they do.
Really this isn’t a security issue, it’s a usability issue. If Microsoft had provided an option in Windows so that the user would be asked to confirm a move then we would all be happy. Unfortunately, they haven’t.
You might be thinking “so what – it’s the user’s fault, they should have been more careful”. However, it’s easy to do. Browse to your favourite search engine and enter Windows Explorer move confirm and you’ll see that plenty of other people have the same problem.
So, Microsoft, why haven’t you fixed this issue? It shouldn’t be hard – you only need to provide a tick box under the Folder Options menu and then, if it’s ticked, ask the user to confirm a drag and drop move. One of your gun Windows programmers could probably knock it up over lunch.
It’s just not good enough!
Anyway, one of the issues we have with Windows is when a user accidentally moves a directory. How do you accidentally move a directory you ask. By moving your mouse across the screen. Sometimes, for one reason or another, as you drag the mouse the left button gets held down and suddenly you’ve moved a directory. If it’s a small directory the user may not even be aware that they’ve done it – and sometime later we get asked to restore the “missing” directory.
This has happened often enough that I’ve been asked to modify permissions on directories so that users can’t do it. The problem is I can’t – the permissions on the directories are fine. The users concerned are supposed to be able to do what they do.
Really this isn’t a security issue, it’s a usability issue. If Microsoft had provided an option in Windows so that the user would be asked to confirm a move then we would all be happy. Unfortunately, they haven’t.
You might be thinking “so what – it’s the user’s fault, they should have been more careful”. However, it’s easy to do. Browse to your favourite search engine and enter Windows Explorer move confirm and you’ll see that plenty of other people have the same problem.
So, Microsoft, why haven’t you fixed this issue? It shouldn’t be hard – you only need to provide a tick box under the Folder Options menu and then, if it’s ticked, ask the user to confirm a drag and drop move. One of your gun Windows programmers could probably knock it up over lunch.
It’s just not good enough!
Virtualisation, Disaster Recovery and Licence Servers
I’m big on virtualisation. I think it’s the way of the future, especially from a DR perspective. The combination of VMware ESX and SAN replication means that the downtime due to the loss of a data centre can be minimised. Virtualisation potentially makes DR a lot easier. As a matter of fact, I think it’s worth virtualising everything, even if you only run one virtual server per physical server. VMware ESXi is now free so it doesn’t even have to cost anything to do it. In my mind it makes a compelling argument.
The only fly in the ointment is the problem of those products that won’t work without a licence server. Some products require a USB or parallel port dongle. They obviously can’t be virtualised.
However, licence servers that don’t require dongles (e.g. FlexLM based) are prime candidates for virtualisation. We can virtualise these servers and know that if we have to fail over to our backup data centre everything will still work.
Intergraph now require a licence server if we want to use their SmartPlant Materials (formerly called Marian) product. Thta’s fine, it’s their product. Unfortunately, they won’t allow us to virtualise the licence server. To my mind, this means that Intergraph are saying that they don’t care about us or our business.
It’s just not good enough!
The only fly in the ointment is the problem of those products that won’t work without a licence server. Some products require a USB or parallel port dongle. They obviously can’t be virtualised.
However, licence servers that don’t require dongles (e.g. FlexLM based) are prime candidates for virtualisation. We can virtualise these servers and know that if we have to fail over to our backup data centre everything will still work.
Intergraph now require a licence server if we want to use their SmartPlant Materials (formerly called Marian) product. Thta’s fine, it’s their product. Unfortunately, they won’t allow us to virtualise the licence server. To my mind, this means that Intergraph are saying that they don’t care about us or our business.
It’s just not good enough!
IBM Blade (mis)Management – Disabled External Ports
We have an IBM Blade Center with two Management Modules, two Nortel Ethernet switches and two Brocade Fibre Channel switches.
The Management modules are used to provide the I/O Modules (the Ethernet and Fibre Channel switches) with basic network configuration (IP address, etc.). The rest of the configuration of the I/O Modules is done directly on the modules themselves (i.e. via telnet or a web browser and Java).
We have had an issue with the Blade Center where after an outage the external ports on the I/O Modules come up disabled. I had to connect to each of the modules and enable to external ports. Now, the first time this happened I assumed that some twit (me) had forgotten to save the configuration of the I/O Modules. So, of course I made extra sure that I saved the configuration.
The next outage we had the same thing happened. The external ports where disabled. However, it was obvious that the configuration had been saved because all the other settings (VLANs, etc.) were correct.
Later I discovered by accident that there’s a setting in the Management Module that overrides the I/O Modules. This setting is tucked away in the Admin/Power/Restart screen when all other configuration is access via the Configuration screen (or by connecting to the modules directly). And it seems that this setting defaults to disabled (although I can’t confirm that):
Now, I can perhaps think of a reason for allowing the Management Module to override the I/O Modules (maybe – if you want to disable all external I/O to a particular module, although we can do that by connecting to the modules themselves, the place where we would normally configure them). But why default to disabled? And if we enable the ports on the I/O modules themselves, shouldn’t the above setting also change to enabled?
It’s just not good enough!
The Management modules are used to provide the I/O Modules (the Ethernet and Fibre Channel switches) with basic network configuration (IP address, etc.). The rest of the configuration of the I/O Modules is done directly on the modules themselves (i.e. via telnet or a web browser and Java).
We have had an issue with the Blade Center where after an outage the external ports on the I/O Modules come up disabled. I had to connect to each of the modules and enable to external ports. Now, the first time this happened I assumed that some twit (me) had forgotten to save the configuration of the I/O Modules. So, of course I made extra sure that I saved the configuration.
The next outage we had the same thing happened. The external ports where disabled. However, it was obvious that the configuration had been saved because all the other settings (VLANs, etc.) were correct.
Later I discovered by accident that there’s a setting in the Management Module that overrides the I/O Modules. This setting is tucked away in the Admin/Power/Restart screen when all other configuration is access via the Configuration screen (or by connecting to the modules directly). And it seems that this setting defaults to disabled (although I can’t confirm that):
 |
| I/O Modules Advanced Setup |
Now, I can perhaps think of a reason for allowing the Management Module to override the I/O Modules (maybe – if you want to disable all external I/O to a particular module, although we can do that by connecting to the modules themselves, the place where we would normally configure them). But why default to disabled? And if we enable the ports on the I/O modules themselves, shouldn’t the above setting also change to enabled?
It’s just not good enough!
Passwords for IBM Remote Supervisor Adapter II
Ah IBM. Their Remote Supervisor Adapter II allows for the creation of up to 12 login ids. The problem is, when you create a password it doesn’t tell you if the password is too long. From trial and error, it seems that the maximum password length is 15 characters. I’ve looked at the source code of the page and I can see that the password field is restricted to that many characters (perhaps I should have saved myself a lot of trail and error testing by looking at the source first):
Now 15 characters isn’t that bad (plenty of systems allow only 8 and it seems one UK bank only allows six). The problem is that it lets you think you have created a password with more than 15 characters – but it only stores the first 15 characters. So, if you set your password to a123456789012345 you can’t login using that password (however, you can login using a12345678901234). Imagine the consequences if this is the only log in account, and you don’t realise the 15 character limit.
Surely it couldn’t have been that hard for the programmer creating the page to have done a basic check and popped up an error message if the password is too long. After all a message does appear if the password doesn’t contain both alphabetic and non alphabetic characters:
So, if they can pop up an error when the password isn’t complex then why can’t they pop up an error when the password is too long.
It’s just not good enough!
 |
| RSA II Password Length - HTML Code |
Now 15 characters isn’t that bad (plenty of systems allow only 8 and it seems one UK bank only allows six). The problem is that it lets you think you have created a password with more than 15 characters – but it only stores the first 15 characters. So, if you set your password to a123456789012345 you can’t login using that password (however, you can login using a12345678901234). Imagine the consequences if this is the only log in account, and you don’t realise the 15 character limit.
Surely it couldn’t have been that hard for the programmer creating the page to have done a basic check and popped up an error message if the password is too long. After all a message does appear if the password doesn’t contain both alphabetic and non alphabetic characters:
 |
| RSA II Password Error |
It’s just not good enough!
Control-F in Microsoft Outlook
In virtually every application I use, including Lotus Notes, Control-F brings up the Find dialogue. This seems to be the default behaviour for Windows applications. There is an exception though – Microsoft Outlook. In Outlook 2007, Control-F is the keyboard shortcut to forward a message. So, Microsoft has broken their own UI standard. Why? They didn’t need to, they already have a keyboard shortcut for forwarding – Alt-W.
Unfortunately, it appears that the User Interface Hall of Shame isn’t being maintained any more. Otherwise this would rate a mention.
It’s just not good enough!
Unfortunately, it appears that the User Interface Hall of Shame isn’t being maintained any more. Otherwise this would rate a mention.
It’s just not good enough!
Prioritisation of Traffic in WAFS and WDC Tunnels on a Packeteer
You just gone out and spent all your money on a fleet of Packeteer iShapers (or PacketShapers and iShared) and want to use them to optimise your network. So, you plan to run cram as much TCP traffic down your WDC tunnel as possible to make the most of your expensive bandwidth. Of course, some traffic is more important than others, so you also plan to prioritise some of your traffic that’s going through the tunnel. It’s a great plan. Unfortunately, it’s a plan that won’t work.
The Packeteer PacketShapers (or the Inline plane in the iShapers) uses WCCP to redirect traffic destined to go through the WDC or WAFS tunnels. It does this before the traffic passes through its inspection and classification engine. That’s fair enough – you don’t want to be needlessly shaping traffic before it reaches the tunnel or you wouldn’t gain any benefits from the WDC cache.
The problem is that once the data has entered the WDC or WAFS tunnel, the PacketShaper (or the Inline plane) thinks it’s just WDC or WAFS traffic. It can’t classify it any further. So you can’t tell whether its the Payroll Department trying to use Oracle to get everyone paid, BITS updating an SMS repository or someone skiving off in Facebook. That means you can’t prioritise one over the other. The whole reason for buying a PacketShaper has just gone out the window. You would actually have been better off using the PacketShaper with a caching device from one of Packeteers competitors (Cisco, Citrix, Riverbed, etc.).
It’s just not good enough!
The Packeteer PacketShapers (or the Inline plane in the iShapers) uses WCCP to redirect traffic destined to go through the WDC or WAFS tunnels. It does this before the traffic passes through its inspection and classification engine. That’s fair enough – you don’t want to be needlessly shaping traffic before it reaches the tunnel or you wouldn’t gain any benefits from the WDC cache.
The problem is that once the data has entered the WDC or WAFS tunnel, the PacketShaper (or the Inline plane) thinks it’s just WDC or WAFS traffic. It can’t classify it any further. So you can’t tell whether its the Payroll Department trying to use Oracle to get everyone paid, BITS updating an SMS repository or someone skiving off in Facebook. That means you can’t prioritise one over the other. The whole reason for buying a PacketShaper has just gone out the window. You would actually have been better off using the PacketShaper with a caching device from one of Packeteers competitors (Cisco, Citrix, Riverbed, etc.).
It’s just not good enough!
Remote Management of a Packeteer iShaper
You could dedicate a whole site to the problems with this product. However, lets start with just one.
The iShaper is basically a melding of the Packeteer PacketShaper and the Packeteer iShared (a product Packteer acquired through their takeover of Tacit Networks). It consists of two planes – the Inline plane which offers the traditional features of the PacketShaper (QoS and not very good reporting) and the Advanced Services plane which runs Windows and offers WAFS and TCP caching (WDC). On paper this device looks a million dollars. The idea is that you can deploy it to a branch office and have it provide the features of a Windows server (Active Directory, DNS, DHCP, printing) together with WAFS, WDC and your traditional PacketShaper QoS. The PacketShaper part (the Inline plane) does a WCCP redirection to the Advanced Services plane of the traffic that needs to go via the WAFS or WDC tunnels. Note that these devices are pretty expensive – depending on your discounts, a mid range server from a tier one vendor is probably cheaper.
One of the problems with this device is that it doesn’t come with any form of built in remote management of the hardware. If you go out and buy a mid range HP Proliant or IBM xServer you’ll have the option of iLO or RSA to provide remote management of power and a remote console. The remote consoles might be slow because they use a Java client and the tracking of the mice might be poor, but at least you can do it. So, if Windows locks up and RDP doesn’t respond, and the server’s in another country, you can try to fix it.
Not so with the iShaper. They have nothing like iLO or RSA (or DRAC in the case of Dells). If RDP doesn’t work you’re stuffed. If the Advanced Services plane stops responding to the network (and that does happen) you’re stuffed.
Because the Inline plane is basically a separate machine it will still respond. You can still
log on and you can use the reset command. However, you can only reset the Inline plane, not the Advanced Services plane. So, you’re still stuffed.
Packeteer now sells an external IP KVM you can use to access the console. Unfortunately, this device only went on sale some considerable time after the release of the iShaper – and it’s not integrated. Nor does it do anything about the power. If Windows were to have a BSOD you would still be stuffed! This does assume that you can get to the KVM. Sometimes a misbehaving iShaper does strange things to the traffic passing through it – like blocking most of it.
My advice, avoid the iShaper. It’s just not good enough!
The iShaper is basically a melding of the Packeteer PacketShaper and the Packeteer iShared (a product Packteer acquired through their takeover of Tacit Networks). It consists of two planes – the Inline plane which offers the traditional features of the PacketShaper (QoS and not very good reporting) and the Advanced Services plane which runs Windows and offers WAFS and TCP caching (WDC). On paper this device looks a million dollars. The idea is that you can deploy it to a branch office and have it provide the features of a Windows server (Active Directory, DNS, DHCP, printing) together with WAFS, WDC and your traditional PacketShaper QoS. The PacketShaper part (the Inline plane) does a WCCP redirection to the Advanced Services plane of the traffic that needs to go via the WAFS or WDC tunnels. Note that these devices are pretty expensive – depending on your discounts, a mid range server from a tier one vendor is probably cheaper.
One of the problems with this device is that it doesn’t come with any form of built in remote management of the hardware. If you go out and buy a mid range HP Proliant or IBM xServer you’ll have the option of iLO or RSA to provide remote management of power and a remote console. The remote consoles might be slow because they use a Java client and the tracking of the mice might be poor, but at least you can do it. So, if Windows locks up and RDP doesn’t respond, and the server’s in another country, you can try to fix it.
Not so with the iShaper. They have nothing like iLO or RSA (or DRAC in the case of Dells). If RDP doesn’t work you’re stuffed. If the Advanced Services plane stops responding to the network (and that does happen) you’re stuffed.
Because the Inline plane is basically a separate machine it will still respond. You can still
log on and you can use the reset command. However, you can only reset the Inline plane, not the Advanced Services plane. So, you’re still stuffed.
Packeteer now sells an external IP KVM you can use to access the console. Unfortunately, this device only went on sale some considerable time after the release of the iShaper – and it’s not integrated. Nor does it do anything about the power. If Windows were to have a BSOD you would still be stuffed! This does assume that you can get to the KVM. Sometimes a misbehaving iShaper does strange things to the traffic passing through it – like blocking most of it.
My advice, avoid the iShaper. It’s just not good enough!
Outlook, HTML, Plain Text and Replies
I currently use Microsoft Outlook 2007 at work. On the whole, it’s ok, but sometimes I do find it frustrating. The problem I’m having at the moment is when I try to reply to an email and I want to make inline comments.
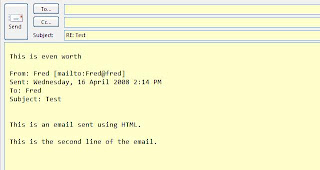
Now it appears that Outlook replies in what ever format the original email was sent in. That’s fine if the original email was plain text. Then each line in the original email will be indented and prefixed with the “>” character. I can just add my comments where I want:
However, if the original email was sent in HTML, then my reply will be in HTML. The problem with that is that it’s less obvious where my comments are:
I can convert the reply to plain text. But that’s even worse as I don’t get the indenting:
It shouldn’t be this hard. It’s just not good enough.
Now it appears that Outlook replies in what ever format the original email was sent in. That’s fine if the original email was plain text. Then each line in the original email will be indented and prefixed with the “>” character. I can just add my comments where I want:
However, if the original email was sent in HTML, then my reply will be in HTML. The problem with that is that it’s less obvious where my comments are:
I can convert the reply to plain text. But that’s even worse as I don’t get the indenting:
It shouldn’t be this hard. It’s just not good enough.
Group Policy Connection / Proxy Settings Tattoos Windows
Group Policy allows Windows administrators to centrally control many settings on a workstation. Generally speaking, it’s a good thing.
Group Policy works by updating the registry. It normally does this by setting the appropriate value under one of the following four keys:
HKEY_LOCAL_MACHINE\Software\Policies
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies
HKEY_CURRENT_USER\Software\Policies
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies
When the policy is removed, the corresponding values are also removed. When the user runs an application that uses group policies, the application should look under the appropriate key above for the policies.
Group Policy can also write directly to the registry. This is common for security settings, or where an application isn’t policy aware (and so won’t look for its settings under the Policies registry keys above). However, when writing outside the Policies keys, the changes are permanent – the settings won’t be removed if the policy is removed. This is called “tattooing”. More information on tattooing can be found in the excellent FAQ at gpoguy.com.
Now, Internet Explorer proxy settings can be configured using Group Policy. This is good as it means that an enterprise can easily configure all its hosts with the appropriate proxy settings. Unfortunately, these settings are tattooed. Why is this unfortunate. Because, when a user leaves the network, the proxy settings still apply. So, if a user takes their laptop home, to a client, to a hotel, etc. and then attempts to browse the Internet they’ll have a problem. They will need to manually disable the proxy.
Why did Microsoft decide to tattoo these settings? I don’t know, but it’s just not good enough.
Group Policy works by updating the registry. It normally does this by setting the appropriate value under one of the following four keys:
HKEY_LOCAL_MACHINE\Software\Policies
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies
HKEY_CURRENT_USER\Software\Policies
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies
When the policy is removed, the corresponding values are also removed. When the user runs an application that uses group policies, the application should look under the appropriate key above for the policies.
Group Policy can also write directly to the registry. This is common for security settings, or where an application isn’t policy aware (and so won’t look for its settings under the Policies registry keys above). However, when writing outside the Policies keys, the changes are permanent – the settings won’t be removed if the policy is removed. This is called “tattooing”. More information on tattooing can be found in the excellent FAQ at gpoguy.com.
Now, Internet Explorer proxy settings can be configured using Group Policy. This is good as it means that an enterprise can easily configure all its hosts with the appropriate proxy settings. Unfortunately, these settings are tattooed. Why is this unfortunate. Because, when a user leaves the network, the proxy settings still apply. So, if a user takes their laptop home, to a client, to a hotel, etc. and then attempts to browse the Internet they’ll have a problem. They will need to manually disable the proxy.
Why did Microsoft decide to tattoo these settings? I don’t know, but it’s just not good enough.
Rant on “Secure Invites”, Malware and Security
Yesterday my brother rang me to say that he was having a problem with his computer (a Toshiba laptop running Windows Vista). He’d been browsing the Internet and clicked yes when asked to install some software so he could view some files. Next think he knows, Internet Explorer is taking him to some website called secureinvites.com and telling him that he’s got a Trojan installed (at least that bit is right) and to buy their security software.
Basically, Secure Invites is a browser hijacker or rogue security software that’s trying to sell rogue anti-spyware software.
While I was helping my brother, he asked why people can get away with this sort of thing. I told him the Internet is like the Wild West. But that’s no excuse. Companies shouldn’t be able to get away with this sort of thing. To me it appears to be fraud. Now, in Australia, there’s no doubt that this would be illegal under the deceptive and misleading conduct provisions of the Trace Practices Act. I don’t know where the parent company for Secure Invites reside but I have no doubt that the people behind it should be in gaol.
I searched the Internet for utilities that would remove Secure Invites. My search on Microsoft didn’t find anything (which is just not good enough). Google turned up a number of results. However, all of them where for domains I wasn’t familiar with. How could I know if a utility was legitimate or more malware? In the end I used SmithfraudFix. It had been listed on a couple of sites and I seemed to recall using it before. I sent my brother the instructions from this page and talked him through it.
We didn’t do the first step however – I asked my brother to back up his files before he did anything. His response – “How do I do that?” When I asked him if he had an external drive, things got a bit vague. In the end it became a case of trusting the removal software and hoping for the best.
So, what’s not good enough:
What’s the solution? I don’t know. But I don’t think it’s user education. Security awareness training has its place in limited situations (e.g. tips on creating secure passwords in combination with systems that will only accept complex passwords), but it’s not practical to educate everyone. Even if we sent every user on a security awareness course, it still wouldn’t work. Some people would still be fooled by a social engineering attack like Secure Invites.
Let's explore the Wild West metaphor I used with my brother. Back in the Wild West, there were plenty of conmen selling snake oil to the gullible. You might say we’re now smarter and don’t buy snake oil. But we do, it’s just that now it’s made out of crystals or just plain water.
So, back to my question, what’s the solution? Well I don’t think there’s a silver bullet. We could deputise a posse to hunt down, torture and string up the malware writers. Of course that might be a little unrealistic (and unethical – cruelty to animals isn’t acceptable).
Perhaps better anti-virus software will help – but based on the industry’s past efforts I think that’s unlikely. Could better designed and built operating systems help? Perhaps it’s an issue that can only be addressed by law enforcement agencies and regulatory authorities.
Who knows? All I know is that it’s just not good enough.
Basically, Secure Invites is a browser hijacker or rogue security software that’s trying to sell rogue anti-spyware software.
While I was helping my brother, he asked why people can get away with this sort of thing. I told him the Internet is like the Wild West. But that’s no excuse. Companies shouldn’t be able to get away with this sort of thing. To me it appears to be fraud. Now, in Australia, there’s no doubt that this would be illegal under the deceptive and misleading conduct provisions of the Trace Practices Act. I don’t know where the parent company for Secure Invites reside but I have no doubt that the people behind it should be in gaol.
I searched the Internet for utilities that would remove Secure Invites. My search on Microsoft didn’t find anything (which is just not good enough). Google turned up a number of results. However, all of them where for domains I wasn’t familiar with. How could I know if a utility was legitimate or more malware? In the end I used SmithfraudFix. It had been listed on a couple of sites and I seemed to recall using it before. I sent my brother the instructions from this page and talked him through it.
We didn’t do the first step however – I asked my brother to back up his files before he did anything. His response – “How do I do that?” When I asked him if he had an external drive, things got a bit vague. In the end it became a case of trusting the removal software and hoping for the best.
So, what’s not good enough:
- This software exists at all
- The people who wrote it and make money from it aren’t being prosecuted
- Windows didn’t protect my brother from this type of software
- Anti-virus software didn’t protect my brother either
- A search of Microsoft’s website didn’t help us
- There was no way for us to verify the bona fides of those sites on the Internet offering a removal tool
- It shouldn’t be so hard for your average computer illiterate user to back up their files
What’s the solution? I don’t know. But I don’t think it’s user education. Security awareness training has its place in limited situations (e.g. tips on creating secure passwords in combination with systems that will only accept complex passwords), but it’s not practical to educate everyone. Even if we sent every user on a security awareness course, it still wouldn’t work. Some people would still be fooled by a social engineering attack like Secure Invites.
Let's explore the Wild West metaphor I used with my brother. Back in the Wild West, there were plenty of conmen selling snake oil to the gullible. You might say we’re now smarter and don’t buy snake oil. But we do, it’s just that now it’s made out of crystals or just plain water.
So, back to my question, what’s the solution? Well I don’t think there’s a silver bullet. We could deputise a posse to hunt down, torture and string up the malware writers. Of course that might be a little unrealistic (and unethical – cruelty to animals isn’t acceptable).
Perhaps better anti-virus software will help – but based on the industry’s past efforts I think that’s unlikely. Could better designed and built operating systems help? Perhaps it’s an issue that can only be addressed by law enforcement agencies and regulatory authorities.
Who knows? All I know is that it’s just not good enough.
Insufficient System Resources and Trend Micro OfficeScan
If you are running Trend Micro OfficeScan with Virus Scan Engine 8.550.1001 you might see errors such as “Insufficient system resources exist to complete the requested service” or “The server was unable to allocate from the system paged pool because the pool was empty.” If you run Poolmon you will see the Vmem tag using around 80 to 100MB of the pool. Basically, this is Trend consuming a large portion of your paged pool:
In Sysinternal's Process Explorer you see that most of your paged memory is in use:
If you unload Trend OfficeScan most of your Kernel’s paged memory is freed:
Basically, it seems that OfficeScan is trying to load its entire pattern file in memory. Unfortunately this file is around 100MB, which doesn’t leave much of the default 160MB page pool for the rest of the system. This problem has been around since at least the end of October when this version of the engine was released. Trend Micro have known about it since at least the middle of December. They have published a work around (see Trend Micro’s Solution ID on the problem) that increases the size of the pool. However, this only delays the onset of the problem.
More information can be found in this thread at the SysInternals forums.
It’s now almost the middle of February and Trend Micro still haven’t released an update fixing this problem. When are they going to fix it? Personally, I think anti-virus can at times be as bad as the viruses.
It’s just not good enough!
In Sysinternal's Process Explorer you see that most of your paged memory is in use:
If you unload Trend OfficeScan most of your Kernel’s paged memory is freed:
Basically, it seems that OfficeScan is trying to load its entire pattern file in memory. Unfortunately this file is around 100MB, which doesn’t leave much of the default 160MB page pool for the rest of the system. This problem has been around since at least the end of October when this version of the engine was released. Trend Micro have known about it since at least the middle of December. They have published a work around (see Trend Micro’s Solution ID on the problem) that increases the size of the pool. However, this only delays the onset of the problem.
More information can be found in this thread at the SysInternals forums.
It’s now almost the middle of February and Trend Micro still haven’t released an update fixing this problem. When are they going to fix it? Personally, I think anti-virus can at times be as bad as the viruses.
It’s just not good enough!
Windows XP and the Classic Start Menu
By default the Start menu in Windows XP looks quite different to Windows 2000. I quite like the new menu – I find it increases my productivity. However, some people prefer the old style Start menu. Nothing wrong with that – Windows XP has an option to change to the “Classic Start menu”.
Now, to reduce training costs (or because the management in IT don’t like change), some organisations want to make the Classic Start menu the default. Again, nothing wrong with that. The problem is that the normal way of doing this is to set the Explorer option NoSimpleStartMenu via the registry or Group Policy (where it’s called “Force classic Start Menu”). Unfortunately, when you set this entry you don’t just make the classic the default, you also disable the new “Simple Start menu” so no-one can use it.
Now I get given my new PC at work. I log in and see the classic Start menu. I then go to change it to the new simple Start menu and I can’t because that option isn’t available anymore. Not happy Jan.
I mean didn’t someone at Microsoft think that perhaps there should be an option to set the classic Start menu as the default but allow users to choose the simple Start menu if they wanted? Would that be such a revolutionary idea?
It’s just not good enough!
Now, to reduce training costs (or because the management in IT don’t like change), some organisations want to make the Classic Start menu the default. Again, nothing wrong with that. The problem is that the normal way of doing this is to set the Explorer option NoSimpleStartMenu via the registry or Group Policy (where it’s called “Force classic Start Menu”). Unfortunately, when you set this entry you don’t just make the classic the default, you also disable the new “Simple Start menu” so no-one can use it.
Now I get given my new PC at work. I log in and see the classic Start menu. I then go to change it to the new simple Start menu and I can’t because that option isn’t available anymore. Not happy Jan.
I mean didn’t someone at Microsoft think that perhaps there should be an option to set the classic Start menu as the default but allow users to choose the simple Start menu if they wanted? Would that be such a revolutionary idea?
It’s just not good enough!
Packeteer PacketShaper, securing interfaces and the MGMT port
Some organisations choose to use a Packeteer PacketShaper on their Internet link. This gives them some rudimentary reporting and the ability to shape their Internet traffic*. When doing this it’s important that the box is secured. One of the steps in securing a PacketShaper is to not allow management access over the outside interface (called securing the interface). Some models also have a MGMT interface. So, why not connect the MGMT interface to the local network and then disable all management access to the Inside and Outside ports. That should allow us to manage the device internally while keeping it safe from all the script kiddies.
Unfortunately, no. To quote the page Specify Security Settings in Packeteer’s PacketGuide:
Now, some might call me stupid (and may do), but for the life of me I cannot think of any reason why the MGMT port should be linked to the Outside interface. I can think of a reason why it shouldn’t – so I can secure the Outside interface and use the MGMT port to manage the device.
What I can’t figure out is why Packeteer decided to do it the way they did.
It’s just not good enough!
* Shaping traffic like streaming video down to less than 1Kbps is popular. It means that IT can hold their hand on their heart and swear to all things holy that they aren’t blocking such traffic – while making such applications unusable.
Unfortunately, no. To quote the page Specify Security Settings in Packeteer’s PacketGuide:
“Enable/disable access to the unit over the inside and/or outside interfaces (for example, ping, Telnet, or web access). The MGMT port (available on certain models) is considered an outside port. Therefore, securing the outside interface will secure the MGMT port as well.”
Now, some might call me stupid (and may do), but for the life of me I cannot think of any reason why the MGMT port should be linked to the Outside interface. I can think of a reason why it shouldn’t – so I can secure the Outside interface and use the MGMT port to manage the device.
What I can’t figure out is why Packeteer decided to do it the way they did.
It’s just not good enough!
* Shaping traffic like streaming video down to less than 1Kbps is popular. It means that IT can hold their hand on their heart and swear to all things holy that they aren’t blocking such traffic – while making such applications unusable.
IBM Remote Supervisor Engine II firmware
I have seen this several times. You buy a new IBM server (perhaps a xSeries 3650) and connect to the Remote Supervisor Adapter. After logging in you get the error:
How hard can it be to ship a server with a working RSA adapter? I mean all they have to do is make sure it has the appropriate firmware.
It’s just not good enough!
The firmware on this ASM does not include functionality to support this server. You can update its firmware on the next page. Click “OK” to continue.See the screen shot below for an example:
How hard can it be to ship a server with a working RSA adapter? I mean all they have to do is make sure it has the appropriate firmware.
It’s just not good enough!
Regional Settings in Windows XP
Why is it that when I select my location as Australia during a Windows
XP install, the installer sets my default language to US English? I
mean, wouldn’t you think that just because I’m in Australia I might want
to default to Australian English?
Subscribe to:
Posts (Atom)